TACACS Definition
TACACS is known as Terminal Access Controller Access Control System, is a remote protocol used to link with a server in networks.
It permits a remote access server to connect with an authentication server to determine if the user has access to the system.
The Defense Data Network developed it for MILNET in the 1980s. It defines in RFC 1492 from 1993 and uses port 49 ( UDP, or TCP ).
A later version of TACACS is XTACACS. Both versions replaced by TACACsPlus (TACACS +, 1995).
Also read: What is Wireshark? – Definition, Uses, Features and More
What are the info about TACACS and its versions?
- TACACS and XTACACS are rarely cast-off. The TACACS + protocol is much better known.
- It is an authentication protocol based on it that has expanded and redefined by Cisco Systems compared to TACACS.
- It is an entirely new protocol and therefore not compatible with TACACS or XTACACS.
- This extension includes a broader selection of authentication methods, the possibility to introduce variable authorization schemes for users.
- It sometimes refers to as tac_plus or T + and is not backward compatible with other versions.
What are the applications?
- It used for central user management for network administrators and operators. Cisco products did not use it exclusively.
- These connect z. B. using Telnet or SSH with the network devices to configure them or perform queries.
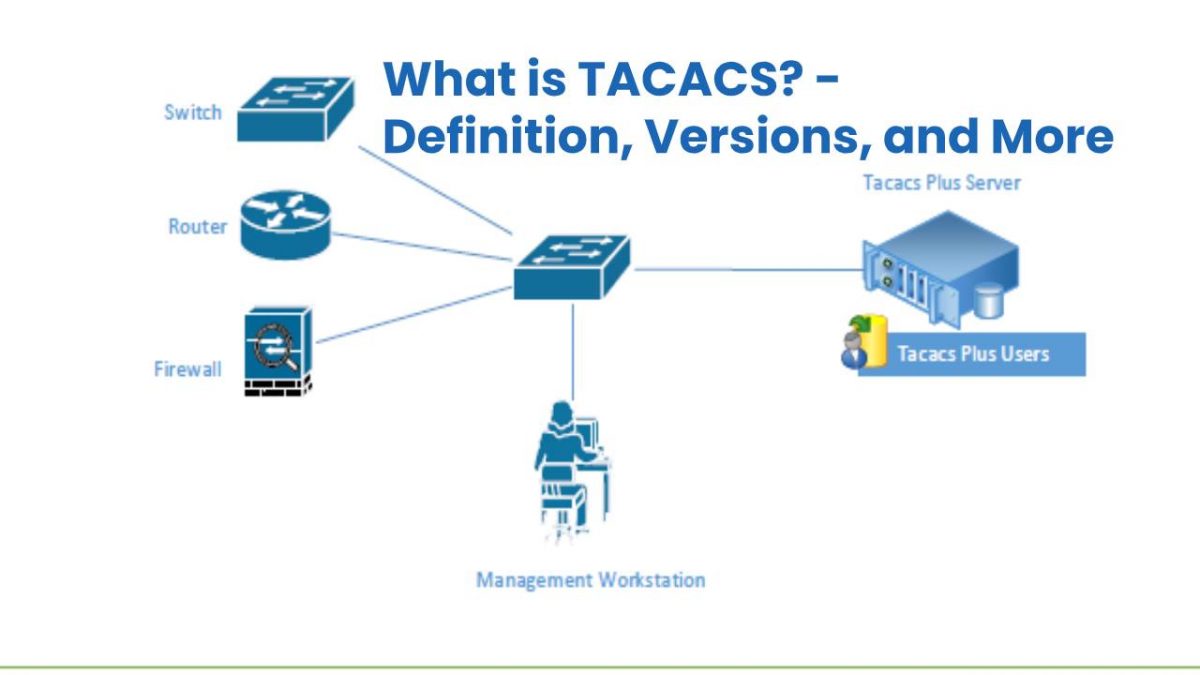
How does TACACS+ work?
- The TACACS+ Server is queried by the client, and the server responds if the user passed or failed authentication.
- It is not indeed the machine from which the user is trying to authenticate, but the device he wants to access, for example, the Switch or Router.
- Whenever a user makes a successful connection to the device, it will ask for their credentials.
- The network device then takes these credentials and validates it with the server.
- And also, This server responds by indicating when the user whether has access to the device or not.
What are the advantages of [TACACS]?
- The password sent encrypted to the server
- Credentials not saved on network devices
- And also, Have a large number of network devices.
- It registers all executed commands
- And also, More protection against brute force attack
- We have a centralized point with managing access levels in a granular way
Also Read: What is a UTM (Unified Threat Management)? – Definition and More
Also You can find more helpful resources at TechiesGuardian
Kamran Sharief
Related posts
Sidebar
Recent Posts
The Rise of Legal Tech Startups: What Law Firms Need to Know
Introduction The legal profession, often rooted in tradition and resistant to change, faces a technological revolution. Legal tech startups are…
Shiba Inu vs. Dogecoin: The Battle of the Meme Coins
In the realm of cryptocurrency, there has been an ongoing battle between two popular meme coins, Shiba Inu and Dogecoin….



Review What is TACACS? – Definition, Versions, and More.