Two-factor Authentication
As you know by now, corporate credentials can be compromised quite easily and represent one of the most dangerous threats to any organization. What makes it extremely dangerous is how difficult it is to detect one of these attacks. The difficulty comes from the fact that once a hacker compromises a set of credentials, they are able to access your network with valid credentials. This means that the security tools you’ve got in place won’t flag anything suspicious, since they will believe that the person logging in is who they say they are.
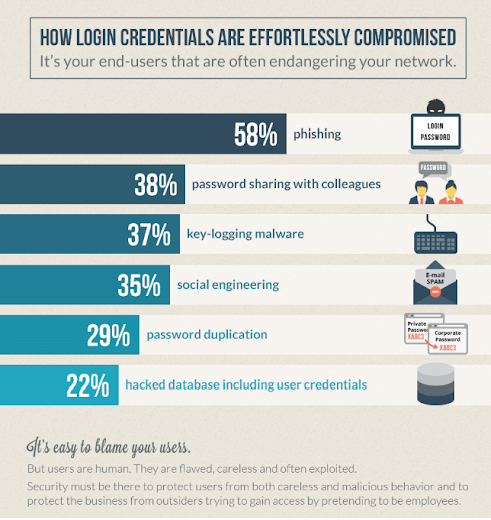
Multifactor Authentication helps with this huge challenge. It is one of the most effective measures to put in place against unauthorized access. Without MFA in place, your other security controls can unfortunately be bypassed.
Most companies know the risk but don’t take it seriously enough. A few years ago, just 38% of companies said they were using MFA according to our research. What’s more worrying is that according to some more recent studies, things haven’t changed so much today. Why is this?
Two-factor Authentication Myths
-
MFA should only be implemented in big companies
Many organizations believe that their company is too small to use MFA. Well, that’s not true. MFA can and should be used by any company, regardless of size. If you think about it, the data small companies want to protect is just as important as any large company. MFA can be adapted to small companies’ needs, it doesn’t have to be complex or expensive.
-
MFA should only be used to protect privileged users
The second thing many organizations believe is that they should use MFA only for their most privileged users. That’s not true either. It should be used to protect every user within an organization. Why is that? Well, many users don’t have access to critical data but they still have access to data that could be used inappropriately and that could harm the organization. Plus, most hackers don’t start with a privileged account, they usually take advantage of a low level easy target to then move laterally within the network.
-
MFA isn’t perfect
Let’s be honest here, in IT security, perfect doesn’t exist. But you need to understand that MFA is pretty close. Some attacks showed MFA could be bypassed. The FBI issued a warning about those attacks. Two authenticator vulnerabilities were the cause: ‘Channel Jacking’, involving taking over the communication channel that is used for the authenticator and ‘Real-Time Phishing’, using a machine-in-the-middle that intercepts and replays authentication messages. However, those attacks need a lot of money and efforts. This is why most of the time, hackers who encounter MFA will change their victim and try to find an easier one.
Despite what happened, the FBI still thinks MFA is highly effective.
-
MFA is too disruptive
There is one challenge when implementing a new solution and that’s to avoid disrupting employee’s productivity. If you don’t take this into consideration, the solution will never be adopted by its users. That’s the reason why MFA needs to be flexible and customized to each organization’s needs. What you can do is combine MFA with contextual controls to further verify identity without disrupting productivity.
Compromised credentials can happen to every user, whether privileged or non-privileged. That’s why MFA should be part of every company’s security strategy, no matter the size.
About the Author

François Amigorena is the founder and CEO of IS Decisions and an expert commentator on cybersecurity issues.
IS Decisions software makes it easy to protect against unauthorized access to networks and the sensitive files within.
Its customers include the FBI, the US Air Force, the United Nations and Barclays — each of which rely on IS Decisions to prevent security breaches; ensure compliance with major regulations; such as SOX and FISMA; quickly respond to IT emergencies; and save time and money for the IT department.
Kamran Sharief
Related posts
Sidebar
Recent Posts
The Rise of Legal Tech Startups: What Law Firms Need to Know
Introduction The legal profession, often rooted in tradition and resistant to change, faces a technological revolution. Legal tech startups are…
Shiba Inu vs. Dogecoin: The Battle of the Meme Coins
In the realm of cryptocurrency, there has been an ongoing battle between two popular meme coins, Shiba Inu and Dogecoin….



Review Two-factor Authentication and the myths that surround it.